Intro Sec Con 2021 CTF Writeup
My writeup on the 2021 Intro Sec Con CTF

Note: Unlike previous writeups, this was assembled after finishing, so it's not in order of completion. Any required files are re-hosted.
Successes
Programming: easy_addr (15)
Solve each mathematical expression and sum the results!
Example: 8+3 9+1 The resulting sums are: 11 and 10 Now we add the results: 11+10 == 21 In this small example, the flag would be 21
FILE: easy_problems.txt
Easy enough. Take the sum of each line and add them all together. This could be done in just a few minutes with a paper and pencil. Looking ahead at the next challenge, it's a significantly longer list. Players are almost certainly intended to automate this.
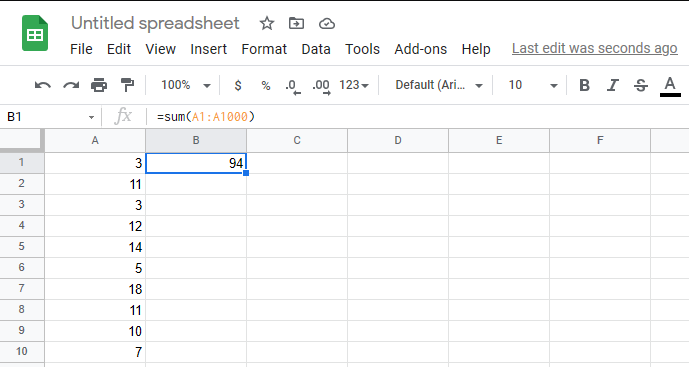
You're probably expecting to see a Bash one-liner here. I found no need for such complexity. Instead, I used my favorite text editor to add = to the beginning of each line. Then I copied and pasted the whole thing into a column in Google Sheets. Now each of those lines evaluates its own sum. I use the SUM() function of Google Sheets to get the total. Work smarter not harder!
Programming: not_so_easy_addr (25)
Solve each mathematical expression and sum the results!
Example: 8+3 9+1 The resulting sums are: 11 and 10 Now we add the results: 11+10 == 21 In this small example, the flag would be 21
FILE: not_so_easy_problems.txt
This is the same as the previous challenge but with more, larger numbers. The method is the same, I just needed to paste more things.
Programming: Big Data (30)
What is the total count of all active users?
FILE: data.json
Looking at a random entry from this file, active is a simple boolean value.
{
"active": true,
"count": 352,
"name": "Oliver",
"friends": [
"Karl",
"Happy",
"Randy",
"Bobby",
"Roper",
"Gabby"
]
}I try simply grepping for true and counting it. No joy.
I try a handful of things to narrow down my search, including getting the whole line ("active": true) but still run into problems. Okay, fine, I'll click the hint.
Note: Use the count field, not the number of users.
One thing that can be frustrating with challenges like these is not truly knowing what some of the data you're looking at means. I don't know what the count means. But let's try extracting it. I use jq to extract just the counts from active users: cat data.json | jq '.["data"][] | select(.active) | .count
This outputs a bunch of numbers. I again SUM() them to get my final answer.
I'm a little disappointed to not really know what's going on here but lacking further context about the data, I was really never going to know exactly what this data is meant to mean.
Programming: Big Data 2 (50)
What is the total count of all active users, who's name is Tommy or are friends with Sam and Sally
(uses same data file as Big Data)
HINT: Note: Use the count field, not the number of users.
This isn't particularly difficult, but it does require that I remember how to play with JSON programmatically. I opt for Python.
This could be written with each test broken out, but there's not any need other than perhaps being more readable.
import json
with open('data.json') as f:
data = json.load(f)
total = 0
for user in data["data"]:
if user['active'] and (user['name'] == 'Tommy' or ("Sam" in user['friends'] and "Sally" in user['friends'])):
total += user['count']
print("Total: " + str(total))Forensics: A picture worth a thousand words (25)
I think there is more than a thousand, but you get the idea.
FILE: Picture.png
On any challenge involving a picture, the first step is always to just look at the picture. In this case, that's not super helpful. The second thing to always try is strings.
Running strings on this file outputs a lot of Lorem ipsum text - far more than a thousand words. Grepping for "flag" easily locates the flag.
Foresnics: Dog (25)
This image seems to have more than
(both files are the same, just different formats)
FILES: Dog.psd, Dog.xcf
These are Photoshop and Gimp files, respectively. Opening these files shows a multiple-layer image. The top layer is a dog picture. The bottom layer, which is almost but not entirely covered by the dog, is a QR code.

The QR code decodes directly into the flag.
Forensics: whatzip (50)
We got this zip file, but it looks like something more
FILE: flag.zip
Unzipping this file reveals a couple of directories. One is called word. Looking into that directory, there's four XML files.
Did you know that docx files are made of zipped XML?
Renaming the zip file to flag.docx creates a valid Word file. Opening that file reveals the flag.
Web: Cookie monster (10)
[Redacted link to a page]
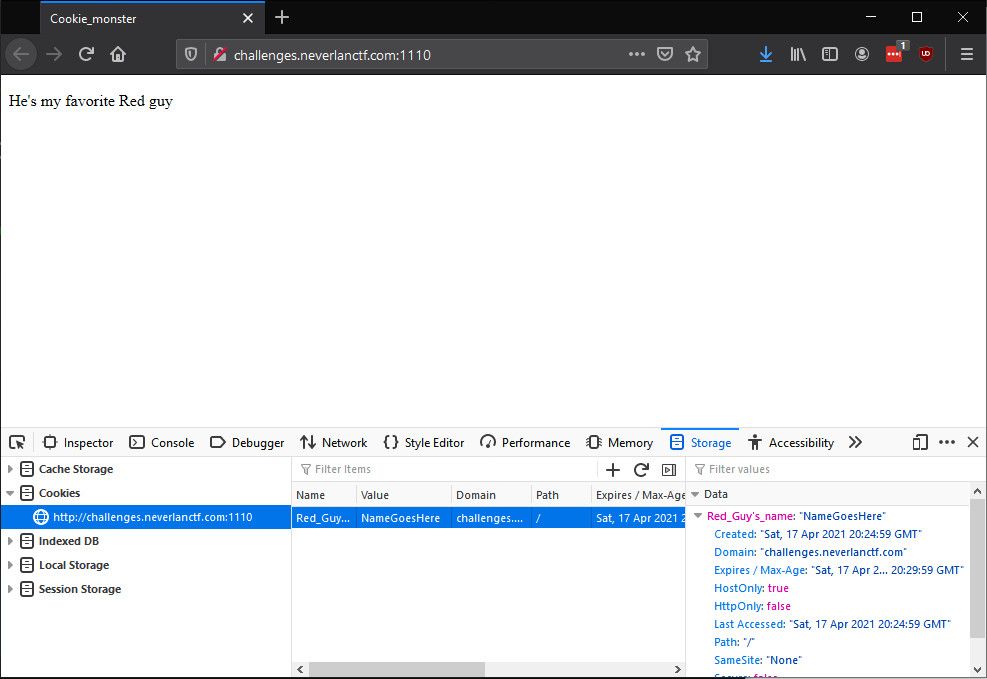
The title of this challenge hints that I should be looking at cookies. Looking at Chrome's Storage tab, I see a cookie with the value NameGoesHere.
Who's Cookie Monster's favorite red guy? Elmo, of course!
Editing the cookie to set the name to Elmo and reloading the page reveals the flag.
Web: JSPassword (10)
The website seems to have a vulnerable login page
[Redacted link to a page]
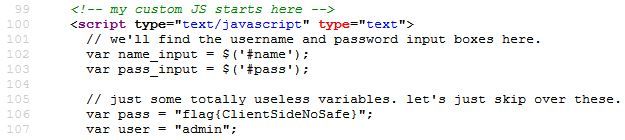
The title of this challenge hints that the problem I'm looking for a flaw in something JavaScript based.
Ctrl+F for script in the source of the page shows inline JavaScript with the flag.
Web: JSPassword2 (15)
This website tried to upgrade it's login, but still hasn't secured it properly
[Redacted link to a page]
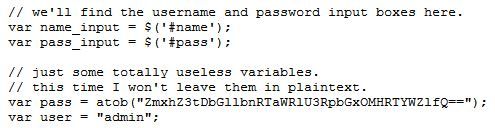
Again the title hints to JavaScript. This time the login code is at /js/login.js. Viewing this code shows the flag that's been Base64 encoded.
Reverse Engineering: Don't over think it (20)
Attached is a binary file, can you get the flag from it?
FILE: reverse
Let's try running this binary first.
It outputs the flag.
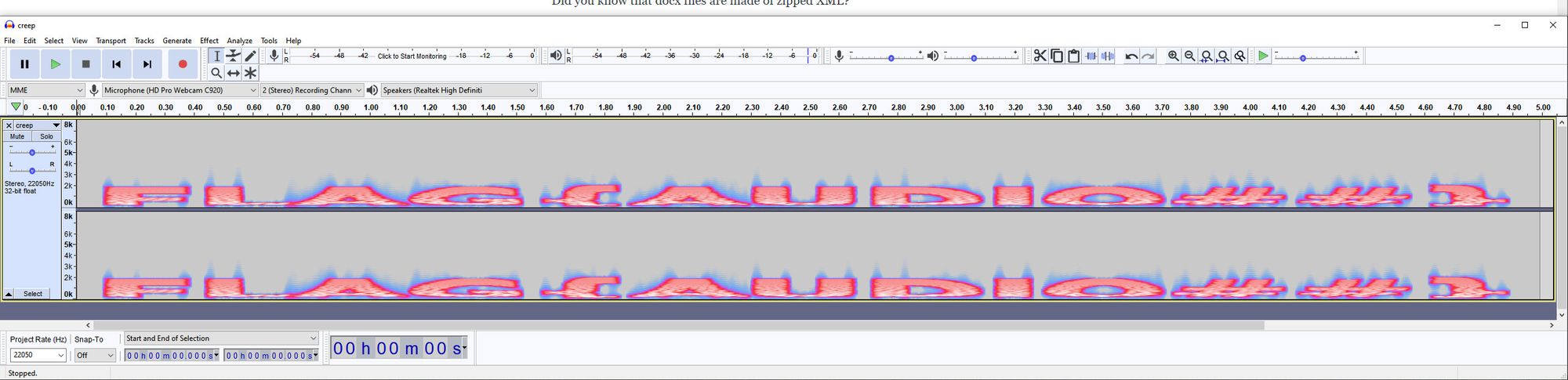
Steganography: creep (50)
Kinda creepy... headphone warning [ :0
FILE: creep.wav
Wave files are another place where there are two things to always check before putting any hard work in. First, try to translate from Morse Code. This file is pretty clearly not Morse, so onto the second always-check. Generate a spectrogram of the audio to see if anything stands out. Sure enough, there's the flag!
Cryptography: cryptopiggie (10)
this is sneakers... he is sneaky
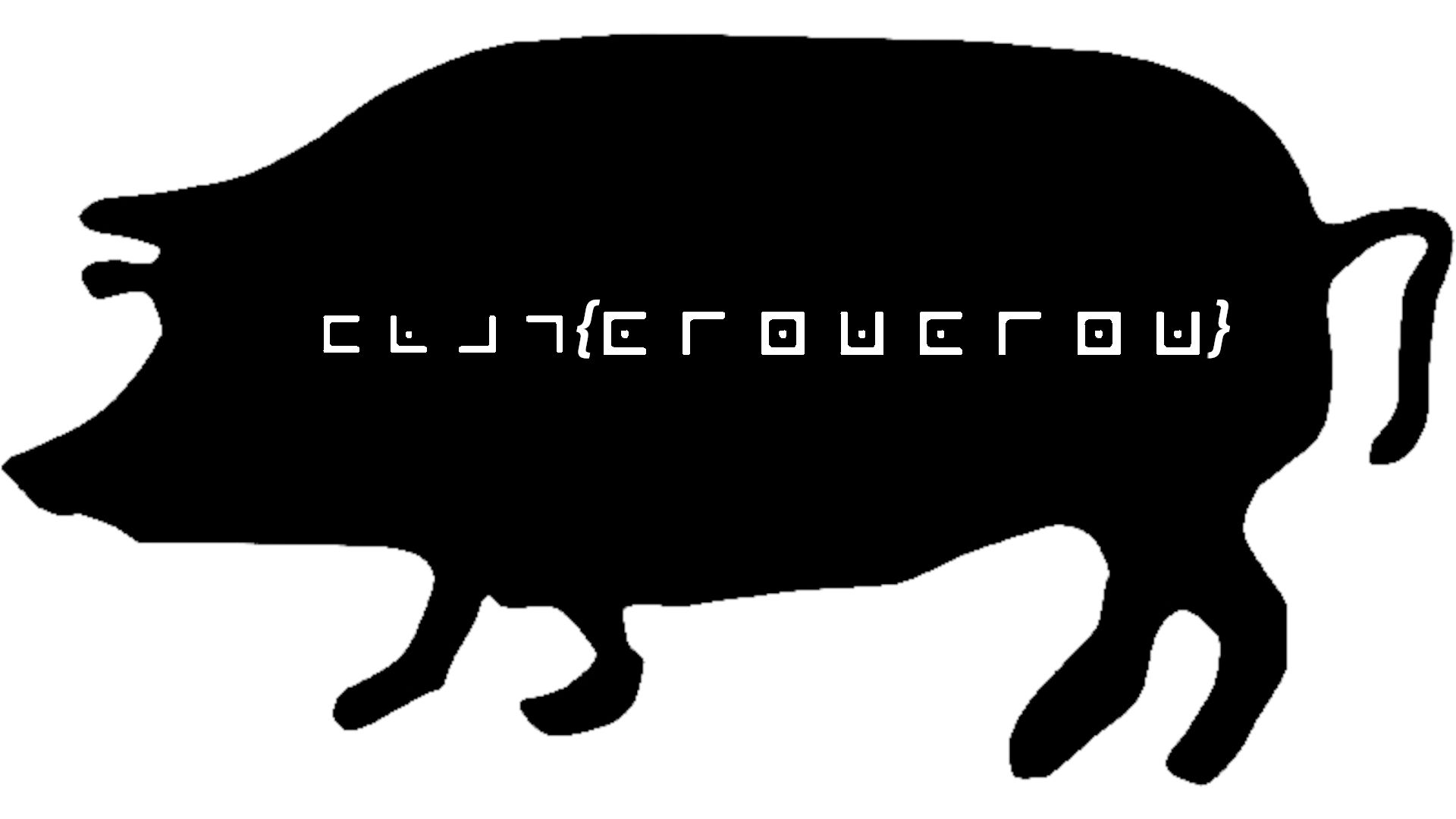
When you see those angles, it's a sure bet that you're looking at the pigpen cipher. The example provided on Wikipedia is the base of the cipher but it is often made more complex by adding a key to the cipher. Rather than proceeding through the symbols alphabetically, start with the key, then add all letters that are missing.
Whether such a key is being used here is easy to determine. Given the format, we know that the first four letters should be FLAG. Using the key on that Wikipedia page confirms that this puzzles doesn't have any complications. I just need to translate from the symbols to letters. As an easy bonus, the four letters of the flag are repeated twice, so only half of the flag needs to be decrypted.
Cryptography: Base your fears (10)
can you decrypt this?ZmxhZ3tUaGVFcXVhbHNHaXZlTWVBd2F5fQ==
When you see something in a CTF that ends in equals signs, it's a good bet that you're looking at something that's been Base64 encoded. Using any Base64 decoding tool will reveal the flag, which pokes a bit of fun at how easy this encoding is to identify.
Cryptography: crypto_salad

This one is slightly less obvious. The image appears to be a Caesar salad, hinting at using the Caesar cipher. The Caesar cipher is another of those techniques that, if you're in the lower point value section of the CTF and you haven't used it yet, you should always check for it.
I like [this site] for working with the Caesar cipher. It will take your cipher text and output all possible Caesar cipher shifts.
This is where I got a bit confused. Decoding the first four characters, which I know are flag, is a +23 shift. But that answer (flag{rubkskgmuujygrgj}) is rejected. Looking at the other shifts, there's another decoding that has plainly visible English text that references the image, but its first four letters are gibberish. Combining the two (ie, flag{the obvious English text}) is accepted as the correct answer.
In progress / fails
I only populate these sections with puzzles that I found especially interesting or frustrating. This time, that's only one:
Lost in the library (75)
FILE: pass.zip
The zip file contains only a JPEG. The image below is only the image portion of the file.

Using strings on the file shows two things that are interesting. A large block of text that has no apparent value and the word hex with a colon after it.
Googling "wall shelf volume page" brings me to the Library of Babel, which is arranged into hexes, then walls, shelves, volumes, and pages. Oh hey, we just had the word hex popup. That's got to be it, right?
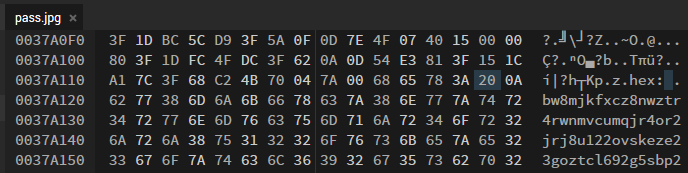
So I'm thinking I need to be in hex 20.
Unfortunately, there's nothing flag-like on hex 20 wall 4 shelf 1 volume 19 page 13. I try a couple of the top strings but nothing goes through.
Maybe that colon (0x3A) is the hex I should be looking for? Same problem there.
About this time, the con was coming to a close, so I gave up. I'm not sure if I chased a wild goose (HONK) here or not. If you happen to know where this was supposed to go, I'd love to find out!
Thanks as always to the con and the CTF runners.